Kubernetes:dashboard 搭建(k8s -web端管理)
本文共 22550 字,大约阅读时间需要 75 分钟。
dashboard版本v2.0.1
github地址:
yaml 地址:
帮助说明:
我的yaml文件git地址:
一,环境准备
k8s安装请参考:
k8s集群:
所需要镜像(提前pull下来,部署时更快)
docker pull kubernetesui/dashboard:v2.0.1
docker pull kubernetesui/metrics-scraper:v1.0.4
二,部署
在网上看过很多帖子,基本都是在拉取yaml时超时。我们这里直接使用github里面的yaml
内容如下
# Copyright 2017 The Kubernetes Authors.## Licensed under the Apache License, Version 2.0 (the "License");# you may not use this file except in compliance with the License.# You may obtain a copy of the License at## http://www.apache.org/licenses/LICENSE-2.0## Unless required by applicable law or agreed to in writing, software# distributed under the License is distributed on an "AS IS" BASIS,# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.# See the License for the specific language governing permissions and# limitations under the License.apiVersion: v1kind: Namespacemetadata: name: kubernetes-dashboard---apiVersion: v1kind: ServiceAccountmetadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboard---kind: ServiceapiVersion: v1metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboardspec: ports: - port: 443 targetPort: 8443 selector: k8s-app: kubernetes-dashboard---apiVersion: v1kind: Secretmetadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-certs namespace: kubernetes-dashboardtype: Opaque---apiVersion: v1kind: Secretmetadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-csrf namespace: kubernetes-dashboardtype: Opaquedata: csrf: ""---apiVersion: v1kind: Secretmetadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-key-holder namespace: kubernetes-dashboardtype: Opaque---kind: ConfigMapapiVersion: v1metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-settings namespace: kubernetes-dashboard---kind: RoleapiVersion: rbac.authorization.k8s.io/v1metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboardrules: # Allow Dashboard to get, update and delete Dashboard exclusive secrets. - apiGroups: [""] resources: ["secrets"] resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"] verbs: ["get", "update", "delete"] # Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map. - apiGroups: [""] resources: ["configmaps"] resourceNames: ["kubernetes-dashboard-settings"] verbs: ["get", "update"] # Allow Dashboard to get metrics. - apiGroups: [""] resources: ["services"] resourceNames: ["heapster", "dashboard-metrics-scraper"] verbs: ["proxy"] - apiGroups: [""] resources: ["services/proxy"] resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"] verbs: ["get"]---kind: ClusterRoleapiVersion: rbac.authorization.k8s.io/v1metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboardrules: # Allow Metrics Scraper to get metrics from the Metrics server - apiGroups: ["metrics.k8s.io"] resources: ["pods", "nodes"] verbs: ["get", "list", "watch"]---apiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboardroleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: kubernetes-dashboardsubjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata: name: kubernetes-dashboardroleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: kubernetes-dashboardsubjects: - kind: ServiceAccount name: kubernetes-dashboard namespace: kubernetes-dashboard---kind: DeploymentapiVersion: apps/v1metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kubernetes-dashboardspec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard spec: containers: - name: kubernetes-dashboard image: kubernetesui/dashboard:v2.0.1 imagePullPolicy: Always ports: - containerPort: 8443 protocol: TCP args: - --auto-generate-certificates - --namespace=kubernetes-dashboard # Uncomment the following line to manually specify Kubernetes API server Host # If not specified, Dashboard will attempt to auto discover the API server and connect # to it. Uncomment only if the default does not work. # - --apiserver-host=http://my-address:port volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs # Create on-disk volume to store exec logs - mountPath: /tmp name: tmp-volume livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 runAsGroup: 2001 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard nodeSelector: "kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule---kind: ServiceapiVersion: v1metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboardspec: ports: - port: 8000 targetPort: 8000 selector: k8s-app: dashboard-metrics-scraper---kind: DeploymentapiVersion: apps/v1metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kubernetes-dashboardspec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: dashboard-metrics-scraper template: metadata: labels: k8s-app: dashboard-metrics-scraper annotations: seccomp.security.alpha.kubernetes.io/pod: 'runtime/default' spec: containers: - name: dashboard-metrics-scraper image: kubernetesui/metrics-scraper:v1.0.4 ports: - containerPort: 8000 protocol: TCP livenessProbe: httpGet: scheme: HTTP path: / port: 8000 initialDelaySeconds: 30 timeoutSeconds: 30 volumeMounts: - mountPath: /tmp name: tmp-volume securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 runAsGroup: 2001 serviceAccountName: kubernetes-dashboard nodeSelector: "kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule volumes: - name: tmp-volume emptyDir: {} 我这里使用源码,什么都不改直接执行下面的命令
kubectl apply -f recommended.yaml
我们可以查看pod 和svc
kubectl get pod,svc -n=kubernetes-dashboardNAME READY STATUS RESTARTS AGEpod/dashboard-metrics-scraper-6b4884c9d5-57gt6 1/1 Running 0 48mpod/kubernetes-dashboard-7bfbb48676-6bmvc 1/1 Running 0 48mNAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGEservice/dashboard-metrics-scraper ClusterIP 10.104.16.268000/TCP 48mservice/kubernetes-dashboard ClusterIP 10.101.110.246 443/TCP 48m
三,登录dashboard
在上面我们看到 地址是10.101.110.246 端口是443
我们在宿主机上使用火狐浏览器 直接访问 :443
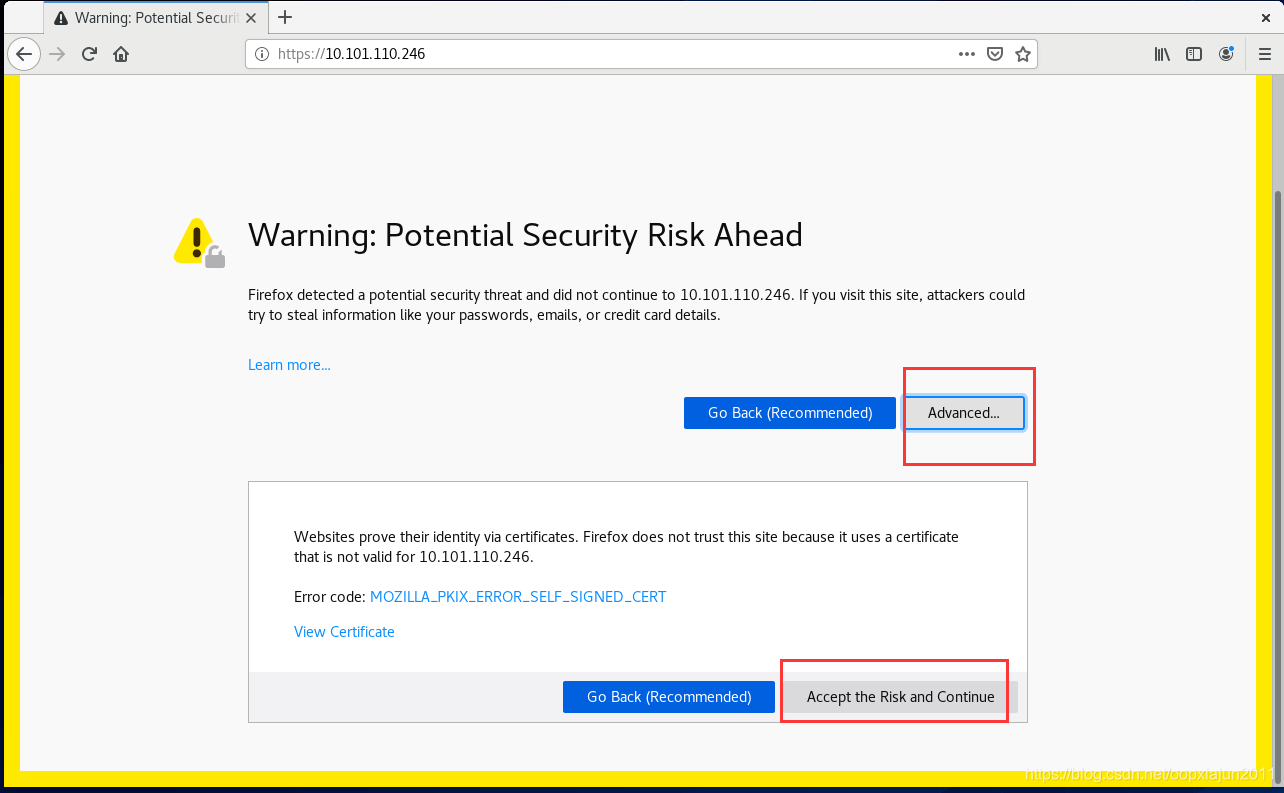
提示我们是有token 或者 kubeconfig 两种登录
Token 登录
我们先看 k8s上有哪些 secrets
kubectl get secretsNAME TYPE DATA AGEdefault-token-pnlhg kubernetes.io/service-account-token 3 48d
然后我们在具体查看token值
kubectl get secrets default-token-pnlhg -o json{ "apiVersion": "v1", "data": { "ca.crt": "LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUN5RENDQWJDZ0F3SUJBZ0lCQURBTkJna3Foa2lHOXcwQkFRc0ZBREFWTVJNd0VRWURWUVFERXdwcmRXSmwKY201bGRHVnpNQjRYRFRJd01EUXhNakExTWpNME9Wb1hEVE13TURReE1EQTFNak0wT1Zvd0ZURVRNQkVHQTFVRQpBeE1LYTNWaVpYSnVaWFJsY3pDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBSkxSCm1nTzNTUkNRWXBCYUhXTm4vV2dxUzN1aGRMR3hlOUpnY0pGRjJQc2hyai9OTGtlN242U2swVSsvZnRYMEkyWmIKdnNPZUJsYXNraTFrb2h0TS9nbk5nTWtzMDdXcWJBanBYOWF0SmRXMm1LYmgvVnlQYXg4RnlXd3oyeXB1bGRhZAo3b3ZuL09xNzVLVys3aWsybUs3MzZjSUd0YXNpTDRTd3hxcFhEeHNFdkN1RFhiOEdlZitYRVNkcEdTMytNaERRCmRIYTFlTlNhRzZYWU93UFZMRG1vOHc0cm14SWEwM0RILzAwTmxNeGFoakF1NVAxdTVhZDg2QUxsbjZzVEw2SWkKYTZmb2d5Wm05R3FENFdWOXJmVjQ3ZGllUnRsUDhFSEs4MmFEM3FiNTZGNWRpVmMvTlFrWm1tV1VzalZtV0Q4MwpkUm8vclF1MkZNRko5MytISEVrQ0F3RUFBYU1qTUNFd0RnWURWUjBQQVFIL0JBUURBZ0trTUE4R0ExVWRFd0VCCi93UUZNQU1CQWY4d0RRWUpLb1pJaHZjTkFRRUxCUUFEZ2dFQkFCRHVTOGVSZ3NqUkpWa2hCYU92Y3BmNGFFS20KRkd0NkF2ejhuZzRTNE1Oc0VnbkFNRFpVZlN4TE9pNzUyaE81WmZHaGxBUFpvK1hjZEZLY2liTHM5a0J5SGpMRAo0dEdFQWhteWh5RjA2VEJ6N09ZVEhOYlZ4TzJIWi9PdjVYYXlmQ1BMeTc0NnVQWlp2Uzd6Tmo5M0JLTjdJbmxvCjUvenBUZVlEZS9UUGozTXB0eHp6UFFBVVh0bUtNbWFVc25NdS9ub0lBNUVrRFJYQVYwQlRnMVhOQ1dTaFVFZDIKaWhMT3ErNG9aZ2pKb1NQZU55WVpjM1RYRHAxVGZaa0FsN2FIS2hnWWpXUkxJRVprc0NWczNDSDVIT3kvNkZxUQpMdFFTT0V6K1FweDRVWVVUaGZhSXE0bEZIZjUvc1VZL2IyenBSRXY0R1l5bThUM3lhbXMvT3RSWVg1TT0KLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=", "namespace": "ZGVmYXVsdA==", "token": "ZXlKaGJHY2lPaUpTVXpJMU5pSXNJbXRwWkNJNklqUXllbGt3U2xKV1VHRTVlbEJ4T0U4MlVESkNOMlZaTjBOaWQzQjFiM1prYjFrd2EwcHNkRnBzVUVVaWZRLmV5SnBjM01pT2lKcmRXSmxjbTVsZEdWekwzTmxjblpwWTJWaFkyTnZkVzUwSWl3aWEzVmlaWEp1WlhSbGN5NXBieTl6WlhKMmFXTmxZV05qYjNWdWRDOXVZVzFsYzNCaFkyVWlPaUprWldaaGRXeDBJaXdpYTNWaVpYSnVaWFJsY3k1cGJ5OXpaWEoyYVdObFlXTmpiM1Z1ZEM5elpXTnlaWFF1Ym1GdFpTSTZJbVJsWm1GMWJIUXRkRzlyWlc0dGNHNXNhR2NpTENKcmRXSmxjbTVsZEdWekxtbHZMM05sY25acFkyVmhZMk52ZFc1MEwzTmxjblpwWTJVdFlXTmpiM1Z1ZEM1dVlXMWxJam9pWkdWbVlYVnNkQ0lzSW10MVltVnlibVYwWlhNdWFXOHZjMlZ5ZG1salpXRmpZMjkxYm5RdmMyVnlkbWxqWlMxaFkyTnZkVzUwTG5WcFpDSTZJakpsTkdKaU9EZ3dMVGRrWlRrdE5HVXdOeTA1WWpJekxUbGlOVE01TW1GaE0ySXlOaUlzSW5OMVlpSTZJbk41YzNSbGJUcHpaWEoyYVdObFlXTmpiM1Z1ZERwa1pXWmhkV3gwT21SbFptRjFiSFFpZlEuQ245bmpEa2FTSy1EUlJUVTRucU9ybU93ZFVab2k5dDhWUjVpXzc2Nlg2dm9tT2R2LWdlenZqWkt4OWlxYkVrOUhlQ1ozQzF1NS1CZVpyMVBsdWZ5aXF1M18xNnM1UUJCYTI3UmxxVHAtaDVyMFBWMW5FRmdwSGhsMXc5MjJXZV83eHVUY1JRUkZoNU83VEMxQVFULU5qalFWRUFvdjRKaHpYVVJhSnZzSFpnOWFUMHQ2RmtxMUpmVDJPbW9pNzhWbFZqNnFlTE9sNkRDdDRJTmFvNFd0c1J1Tm9lQzQzODJCc1J2MjItSHF4M2xBeVM0RlNnaUlyVWhhbU5scWRMbWsyQmZYSXQwSEFxY1Z5M0dhck5RalZvd3ZxZXQ4QXlrWXdBaUNlQWlkTzMzYWhGcGlSdXZkcVhEUDZoNUFCV2d3Nlpmbjk3YThoVmtvVllRZ2JFWE5n" }, "kind": "Secret", "metadata": { "annotations": { "kubernetes.io/service-account.name": "default", "kubernetes.io/service-account.uid": "2e4bb880-7de9-4e07-9b23-9b5392aa3b26" }, "creationTimestamp": "2020-04-12T05:24:33Z", "managedFields": [ { "apiVersion": "v1", "fieldsType": "FieldsV1", "fieldsV1": { "f:data": { ".": {}, "f:ca.crt": {}, "f:namespace": {}, "f:token": {} }, "f:metadata": { "f:annotations": { ".": {}, "f:kubernetes.io/service-account.name": {}, "f:kubernetes.io/service-account.uid": {} } }, "f:type": {} }, "manager": "kube-controller-manager", "operation": "Update", "time": "2020-04-12T05:24:33Z" } ], "name": "default-token-pnlhg", "namespace": "default", "resourceVersion": "361", "selfLink": "/api/v1/namespaces/default/secrets/default-token-pnlhg", "uid": "067fa8f1-fff5-438a-8047-ea0d2c292f9c" }, "type": "kubernetes.io/service-account-token"} 但是这里要用base64位转一次才是可以在界面上输入的token
kubectl get secrets default-token-pnlhg -o jsonpath={.data.token}|base64 -deyJhbGciOiJSUzI1NiIsImtpZCI6IjQyelkwSlJWUGE5elBxOE82UDJCN2VZN0Nid3B1b3Zkb1kwa0psdFpsUEUifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtdG9rZW4tcG5saGciLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjJlNGJiODgwLTdkZTktNGUwNy05YjIzLTliNTM5MmFhM2IyNiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQifQ.Cn9njDkaSK-DRRTU4nqOrmOwdUZoi9t8VR5i_766X6vomOdv-gezvjZKx9iqbEk9HeCZ3C1u5-BeZr1Plufyiqu3_16s5QBBa27RlqTp-h5r0PV1nEFgpHhl1w922We_7xuTcRQRFh5O7TC1AQT-NjjQVEAov4JhzXURaJvsHZg9aT0t6Fkq1JfT2Omoi78VlVj6qeLOl6DCt4INao4WtsRuNoeC4382BsRv22-Hqx3lAyS4FSgiIrUhamNlqdLmk2BfXIt0HAqcVy3GarNQjVowvqet8AykYwAiCeAidO33ahFpiRuvdqXDP6h5ABWgw6Zfn97a8hVkoVYQgbEXNg 这个token值我们复制到输入框就可以登录
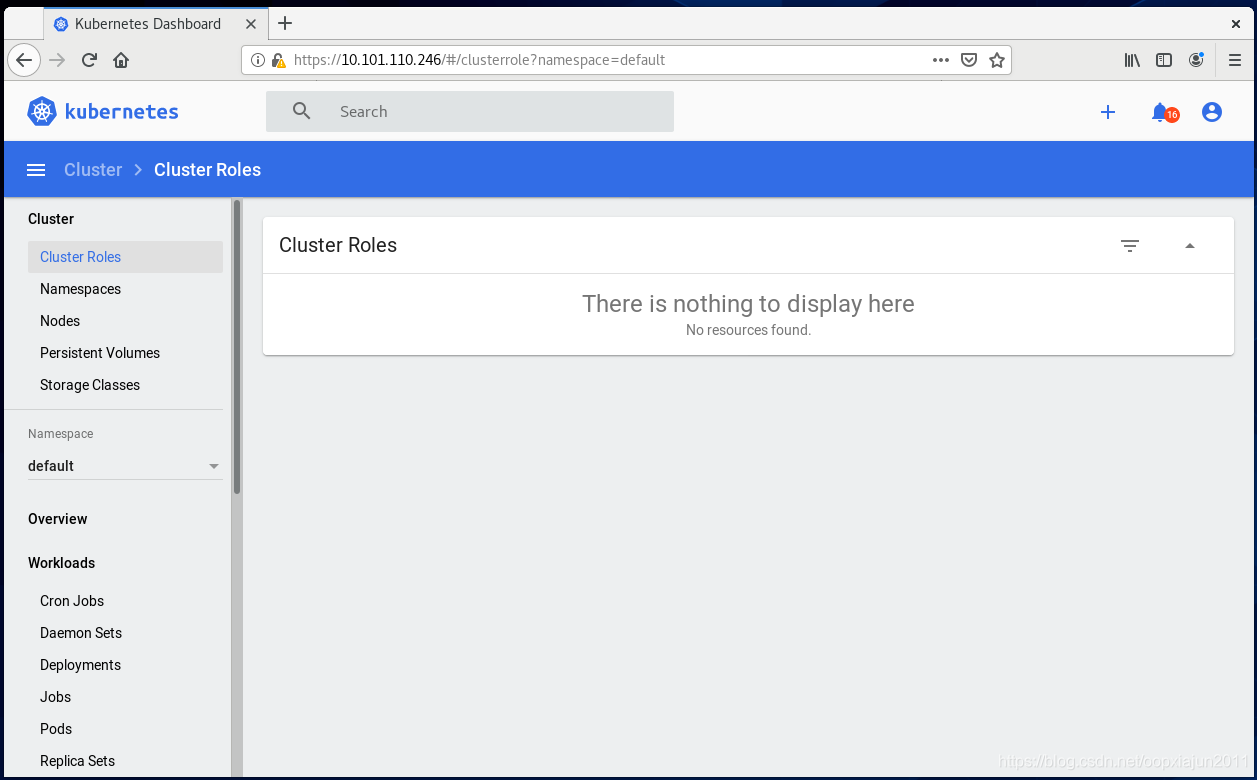
Kubeconfig 登录
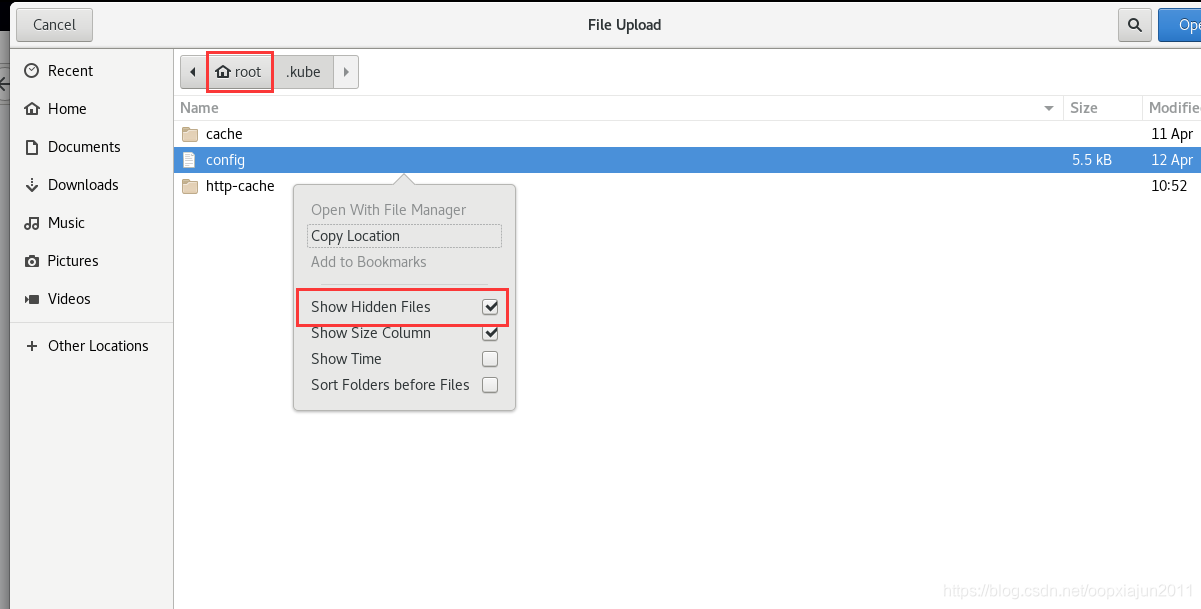
kubeconfig 一般在~/root/.kube/config 里面,(把隐藏文件显示出来【右键就能操作】)
username+Password登录
第一步:创建密码管理文件
# cat /etc/kubernetes/basic_auth_file admin,admin,1 xiajun,1234@abc,2 #前面为用户,后面为密码,数字为用户ID不可重复
第二步:修改kube-apiserver.yaml
#vim /etc/kubernetes/manifests/kube-apiserver.yaml#添加一条密码文件配置--basic-auth-file=/etc/kubernetes/basic_auth_file
第三步 :添加完毕后重启api-server
#添加完毕后重启api-server #kubectl apply -f /etc/kubernetes/manifests/kube-apiserver.yaml
第四步:Deployment.spec.args 添加 内容如下
- --authentication-mode=basic
最后的yaml 内容如下
# Copyright 2017 The Kubernetes Authors.## Licensed under the Apache License, Version 2.0 (the "License");# you may not use this file except in compliance with the License.# You may obtain a copy of the License at## http://www.apache.org/licenses/LICENSE-2.0## Unless required by applicable law or agreed to in writing, software# distributed under the License is distributed on an "AS IS" BASIS,# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.# See the License for the specific language governing permissions and# limitations under the License.# 1:将 namespace 换成 kube-system# 2:将 Server下的 type 设置为 NodePort 类型# 3:不创建 名称空间 为kubernetes-dashboard # apiVersion: v1# kind: Namespace# metadata:# name: kubernetes-dashboard# ---apiVersion: v1kind: ServiceAccountmetadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-system---kind: ServiceapiVersion: v1metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-systemspec: type: NodePort ports: - port: 443 targetPort: 8443 nodePort: 8443 selector: k8s-app: kubernetes-dashboard---apiVersion: v1kind: Secretmetadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-certs namespace: kube-systemtype: Opaque---apiVersion: v1kind: Secretmetadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-csrf namespace: kube-systemtype: Opaquedata: csrf: ""---apiVersion: v1kind: Secretmetadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-key-holder namespace: kube-systemtype: Opaque---kind: ConfigMapapiVersion: v1metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard-settings namespace: kube-system---kind: RoleapiVersion: rbac.authorization.k8s.io/v1metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-systemrules: # # Allow Dashboard to get, update and delete Dashboard exclusive secrets. # - apiGroups: [""] # resources: ["secrets"] # resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"] # verbs: ["get", "update", "delete"] # # Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map. # - apiGroups: [""] # resources: ["configmaps"] # resourceNames: ["kubernetes-dashboard-settings"] # verbs: ["get", "update"] # # Allow Dashboard to get metrics. # - apiGroups: [""] # resources: ["services"] # resourceNames: ["heapster", "dashboard-metrics-scraper"] # verbs: ["proxy"] # - apiGroups: [""] # resources: ["services/proxy"] # resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"] # verbs: ["get"] - apiGroups: ["*"] resources: ["*"] resourceNames: ["*"] verbs: ["*"]---kind: ClusterRoleapiVersion: rbac.authorization.k8s.io/v1metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard #rules: #Allow Metrics Scraper to get metrics from the Metrics server - apiGroups: ["metrics.k8s.io"] resources: ["pods", "nodes"] verbs: ["get", "list", "watch"] - apiGroups: ["*"] resources: ["*"] verbs: ["*"]---apiVersion: rbac.authorization.k8s.io/v1kind: RoleBindingmetadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-systemroleRef: apiGroup: rbac.authorization.k8s.io kind: Role name: kubernetes-dashboardsubjects: # - kind: ServiceAccount # name: kubernetes-dashboard # namespace: kube-system # 全部用户 - kind: Group name: system:authenticated apiGroup: rbac.authorization.k8s.io - kind: Group name: system:unauthenticated apiGroup: rbac.authorization.k8s.io---apiVersion: rbac.authorization.k8s.io/v1kind: ClusterRoleBindingmetadata: name: kubernetes-dashboardroleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: kubernetes-dashboardsubjects: # - kind: ServiceAccount # name: kubernetes-dashboard # namespace: kube-system - kind: Group name: system:authenticated apiGroup: rbac.authorization.k8s.io - kind: Group name: system:unauthenticated apiGroup: rbac.authorization.k8s.io---kind: DeploymentapiVersion: apps/v1metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-systemspec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: kubernetes-dashboard template: metadata: labels: k8s-app: kubernetes-dashboard spec: containers: - name: kubernetes-dashboard image: kubernetesui/dashboard:v2.0.1 imagePullPolicy: Always ports: - containerPort: 8443 protocol: TCP args: - --auto-generate-certificates - --namespace=kube-system #使用用户名加密码方式 # cat /etc/kubernetes/basic_auth_file # admin,admin,1 # xiajun,1234@abc,2 #前面为用户,后面为密码,数字为用户ID不可重复 #vim /etc/kubernetes/manifests/kube-apiserver.yaml #--basic-auth-file=/etc/kubernetes/basic_auth_file \ #添加完毕后重启api-server #kubectl apply -f /etc/kubernetes/manifests/kube-apiserver.yaml #重启api-server - --authentication-mode=basic # Uncomment the following line to manually specify Kubernetes API server Host # If not specified, Dashboard will attempt to auto discover the API server and connect # to it. Uncomment only if the default does not work. # - --apiserver-host=http://my-address:port volumeMounts: - name: kubernetes-dashboard-certs mountPath: /certs # Create on-disk volume to store exec logs - mountPath: /tmp name: tmp-volume livenessProbe: httpGet: scheme: HTTPS path: / port: 8443 initialDelaySeconds: 30 timeoutSeconds: 30 securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 #runAsGroup: 2001 volumes: - name: kubernetes-dashboard-certs secret: secretName: kubernetes-dashboard-certs - name: tmp-volume emptyDir: {} serviceAccountName: kubernetes-dashboard # nodeSelector: # "kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule---kind: ServiceapiVersion: v1metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kube-systemspec: ports: - port: 8000 targetPort: 8000 selector: k8s-app: dashboard-metrics-scraper---kind: DeploymentapiVersion: apps/v1metadata: labels: k8s-app: dashboard-metrics-scraper name: dashboard-metrics-scraper namespace: kube-systemspec: replicas: 1 revisionHistoryLimit: 10 selector: matchLabels: k8s-app: dashboard-metrics-scraper template: metadata: labels: k8s-app: dashboard-metrics-scraper annotations: seccomp.security.alpha.kubernetes.io/pod: 'runtime/default' spec: containers: - name: dashboard-metrics-scraper image: kubernetesui/metrics-scraper:v1.0.4 ports: - containerPort: 8000 protocol: TCP livenessProbe: httpGet: scheme: HTTP path: / port: 8000 initialDelaySeconds: 30 timeoutSeconds: 30 volumeMounts: - mountPath: /tmp name: tmp-volume securityContext: allowPrivilegeEscalation: false readOnlyRootFilesystem: true runAsUser: 1001 #runAsGroup: 2001 serviceAccountName: kubernetes-dashboard # nodeSelector: # "kubernetes.io/os": linux # Comment the following tolerations if Dashboard must not be deployed on master tolerations: - key: node-role.kubernetes.io/master effect: NoSchedule volumes: - name: tmp-volume emptyDir: {} 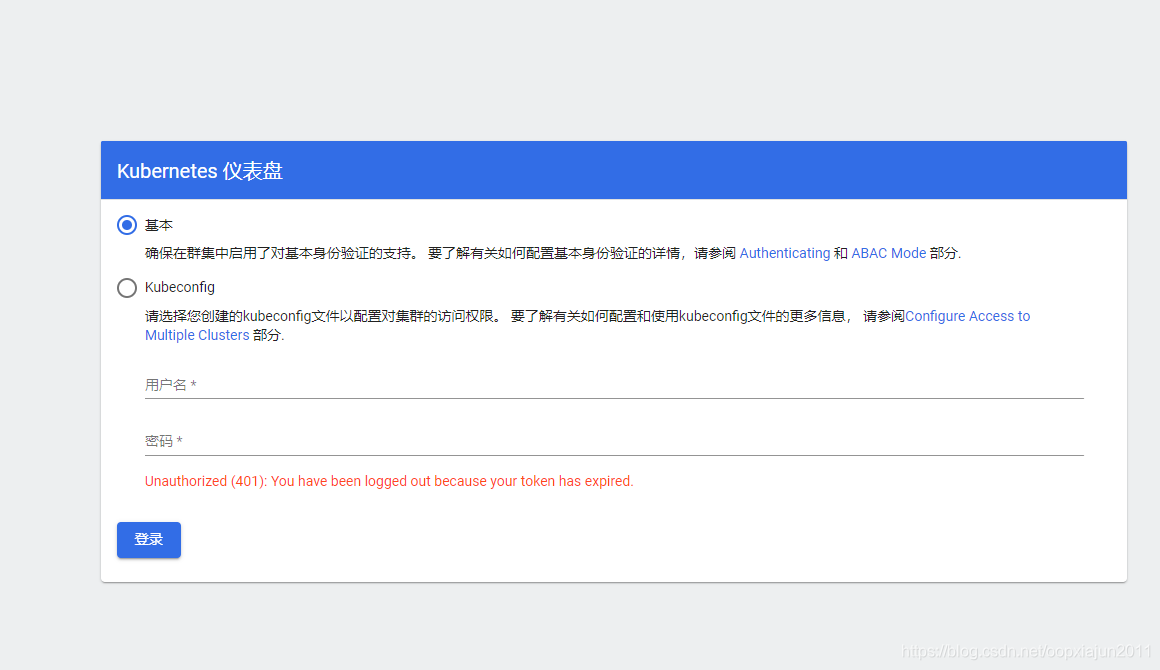
这里面 就能非常容器轻松得构建、部署、发布项目,这儿有三种方式创建

转载地址:http://jzwhz.baihongyu.com/
你可能感兴趣的文章
MySQL批量插入数据遇到错误1213的解决方法
查看>>
mysql技能梳理
查看>>
MySQL报Got an error reading communication packets错
查看>>
Mysql报错Can‘t create/write to file ‘/tmp/#sql_3a8_0.MYD‘ (Errcode: 28 - No space left on device)
查看>>
MySql报错Deadlock found when trying to get lock; try restarting transaction 的问题解决
查看>>
MySQL报错ERROR 1045 (28000): Access denied for user ‘root‘@‘localhost‘
查看>>
Mysql报错Packet for query is too large问题解决
查看>>
mysql报错级别_更改MySQL日志错误级别记录非法登陆(Access denied)
查看>>
Mysql报错:too many connections
查看>>
MySQL报错:无法启动MySQL服务
查看>>
mysql授权用户,创建用户名密码,授权单个数据库,授权多个数据库
查看>>
mysql排序查询
查看>>
MySQL排序的艺术:你真的懂 Order By吗?
查看>>
MySQL排序的艺术:你真的懂 Order By吗?
查看>>
Mysql推荐书籍
查看>>
Mysql插入数据从指定选项中随机选择、插入时间从指定范围随机生成、Navicat使用存储过程模拟插入测试数据
查看>>
MYSQL搜索引擎
查看>>
mysql操作数据表的命令_MySQL数据表操作命令
查看>>
mysql操作日志记录查询_如何使用SpringBoot AOP 记录操作日志、异常日志?
查看>>
MySQL支持的事务隔离级别,以及悲观锁和乐观锁的原理和应用场景?
查看>>